The next
generation telecommunications network (NGN) based on an IP platform
is expected to enable advanced multimedia services such as those in
Table 1.
|
Multiparty
multimedia conferencing |
Multiple
parties interact using voice, media streaming/video, and/or
data. Customers can converse with each other while displaying
visual information. |
|
Collaborative
computing |
Computer
resources, documents, applications, and groupware tools can be
shared for interactive work efforts. |
|
Distance
learning |
Users can
take interactive courses from remote locations. These courses
can be offered in either a computer-based training or live
virtual classroom environment. |
|
Data services |
Real-time
establishment of data connectivity between endpoints, providing
new packet switched circuit flexibility for customers who had
previously been limited to permanent circuits. |
|
Virtual
private network (VPN) |
Data VPN
services expand upon the traditional PSTN VPN services and
provide added security and networking features that allow
customers to use a shared IP network as a closed user group. |
|
Public
network computing |
Businesses
and consumers utilize generic processing and storage
capabilities provided by the network for such activities as
hosting web pages; storage, maintenance, and backup of data; and
applications access. |
|
Information
brokering |
Services that
enable consumers to be matched with providers through
advertising, finding, and providing information. For example,
consumers could receive information based on pre-specified
criteria or based on personal preferences and behavior patterns
in addition to direct subscription. |
|
E-commerce |
Businesses
and consumers can purchase goods and services electronically
over the network. This could include processing transactions,
verifying payment information, providing security, and possibly
trading for goods and services. Consumer services include Home
Banking and Home Shopping. Business-to- business applications
include supply-chain management and knowledge management
applications. |
|
Interactive
games |
Consumers can
meet online and play video games interactively complete with a
set of interactive communication tools. |
Table 1 -
NGN multimedia
services
Within this
context, basically three kinds of applications can be distinguished:
-
·
Elastic applications: Generate discrete media traffic(e.g.
file transfers, www)
-
·
Adaptive applications:
Generate continuous media traffic
(e.g. video and audio),
-
· Critical applications: Generate continuous media traffic
(e.g., teleteaching, teleconferencing, medical telediagnostics,
video/entertainment on demand, and distributed games )
-
· intolerant applications
(e.g., interactive games, some control applications)
-
· tolerant applications
(e.g., interactive voice applications).
In Internet, the
bulk of traffic has so far been generated by elastic
applications. Because the pieces of data exchanged by such
applications are carried over the network as packets that have few
time constraints, we call such traffic discrete media. The
lack of time constraints on the packets allows the network to view
them as loosely coupled. In the Internet, the basic service is
provided by considering the data packets independent of each other
(such packets are called datagrams). Elastic applications are
essentially composed of file transfers.
However, some
elastic applications exhibit a degree of interactivity, and
therefore have additional performance requirements. For instance,
the World Wide Web, the most important application on the Internet
today, makes extensive use of on-demand file transfers between
servers and clients. Because the perceived "quality" of the
transfers depends on the users, their moods, the purpose of the
transfers, as well as many other factors, strict performance
requirements cannot easily be identified.
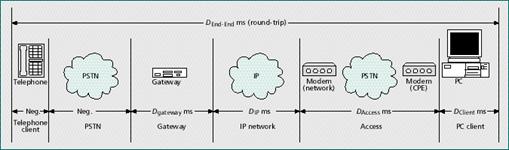
Figure 1 - The
end-to-end delay allocation model for a VoIP PC-phone call.
|
Delay component |
Consumer (objective) |
Business (objective) |
Today (actual) |
Theoretical minimum |
ms above minimum |
|
|
PC client (DClient) |
100 |
30 |
150 |
67.5 |
82.5 |
|
|
Access (DAccess) |
70 |
10 |
150 |
44 |
106 |
|
|
IP network (DIP) |
50 |
30 |
96 |
40 |
56 |
|
|
Gateway POP (DGateway) |
80 |
30 |
160 |
67.5 |
92.5 |
|
|
PSTN/phone (DClient) |
Negligible |
Negligible |
Negligible |
Negligible |
0 |
|
|
Total |
300 |
100 |
556 |
159 |
337 |
|
|
Notes:
1. The
consumer objective is intended to be at the upper bound of
acceptable. The business objective is intended to match PSTN
performance.
2. Today
figures for PC client, access, and gateway point of presence
(POP) are from internal Bell Atlantic testing.
3.
Theoretical minimum figures assume G.723 6.3 kb/s encoding at 2
frames/IP packet, algorithmic delay only. The access figure
further assumes 33.6 kb/s modem connection. The IP network
figure further assumes U.S. coastcoast transport at the speed
of light in metal (~150,0000 km/s). |
|
Table 2 -
VoIP round-trip delay allocation and current performance in
milliseconds.
In addition to
discrete media, applications increasingly make use of continuous
media, due to advances in coding technology and the availability
of multimedia computers. In continuous media, specifically video and
audio, the data have intrinsic temporal and spatial relationships
that must be respected for these forms of data to make sense. The
performance requirements of continuous media are closely linked to
their perceived quality.
Techniques have
been devised whereby the playout quality of continuous media is
adjusted to match the instantaneous capabilities of a system, and in
particular of a network. Such techniques, used by adaptive
applications, allow the use of multimedia applications on
best-effort IP networks-Internet. However, even the best adaptive
techniques are powerless when facing the poorest conditions in a
network; and, as a consequence, guarantees cannot generally be given
as to the quality delivered by adaptive applications on best-effort
networks.
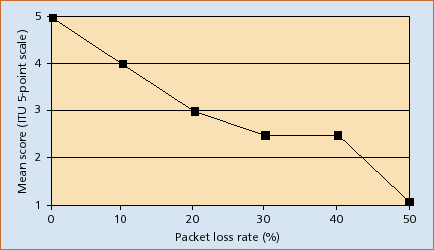
Figure 2 - Voice
quality as a function of packet loss rate
On the other
hand, in order that distributed multimedia applications become
ubiquitous, especially in a commercial environment, there is a need
for a communication platform that is able to provide better control
and guarantees over performance. Especially for commercial use of
applications such as
-
·
teleteaching,
-
·
teleconferencing,
-
·
medical telediagnostics,
-
·
video/entertainment on demand, and
-
·
distributed games,
For these
applications, starting a communication session may be worthwhile
only if some minimum performance can be guaranteed throughout its
duration. These can collectively be called critical applications.
Critical applications can further be classified into intolerant
applications, which do not tolerate any deviation from their
expressed requirements (e.g., interactive games, some control
applications), and tolerant applications, which essentially
have nominal requirements but use adaptive techniques to deal with
occasional violations of these requirements (e.g., interactive voice
applications).
Typically, the
requirements of critical applications can be expressed as a (sub)set
of values representing
-
·
bandwidth,
-
·
delay,
-
·
jitter, and
-
·
packet loss rate
constraints for
the network. For the VoIP application, the influence of some of
these QoS parameters is in Table 2 and Figure 2. In order to be able
to meet these constraints throughout the lifetime of a communication
session, the components of the network (or at least the subset
representing those "manipulating" the packets of the session) must
be aware of their values and must cooperate in taking actions to
enforce these bounds. To that end, in order to enforce the traffic
constraints of a session, a network component has to take part in
some or all of the following general activities:
-
admission control,
-
resource reservation,
-
packet scheduling,
-
traffic policing, and
-
signaling.
It should be
clear that because of their very different characteristics, elastic,
adaptive, and critical applications cover separate regions of a wide
spectrum of demand. In other words, these different types of
application complement, rather than compete with, each other. A
telecommunications infrastructure will therefore have to support all
of them simultaneously and, if possible, seamlessly. This calls for
the design of a network where the overhead associated with each type
of application is no greater than necessary. In the next section we
review potentially promising approaches to providing such support in
the Internet. The common perceived conjecture is that these, in
combination, may provide the sort of support required by the
spectrum of applications.
|